This is specifically for the Redis Challenge. For debugging test failures for common challenges, refer to our guide.
Required Tools
The easiest way to debug problems with your redis implementation is to compare it to the official implementation. To do this, we’ll need a few tools handy.redis-cli, redis-server
Make sure you have redis-cli and redis-server installed. We’ll use redis-cli to test commands against your redis implementation, and redis-server as a reference to compare with.Wireshark
Since redis-cli & redis-server communicate with each over using TCP, we’ll need a tool to inspect TCP messages. Install Wireshark. If you prefer CLI tools you can also use tcpdump.Methodology
1. Setup Wireshark to capture and display TCP traffic
Run Wireshark and usetcp.port == 6379 or tcp.port == 6380 as a display filter. We’ll use this in step 4 to view captured packets.
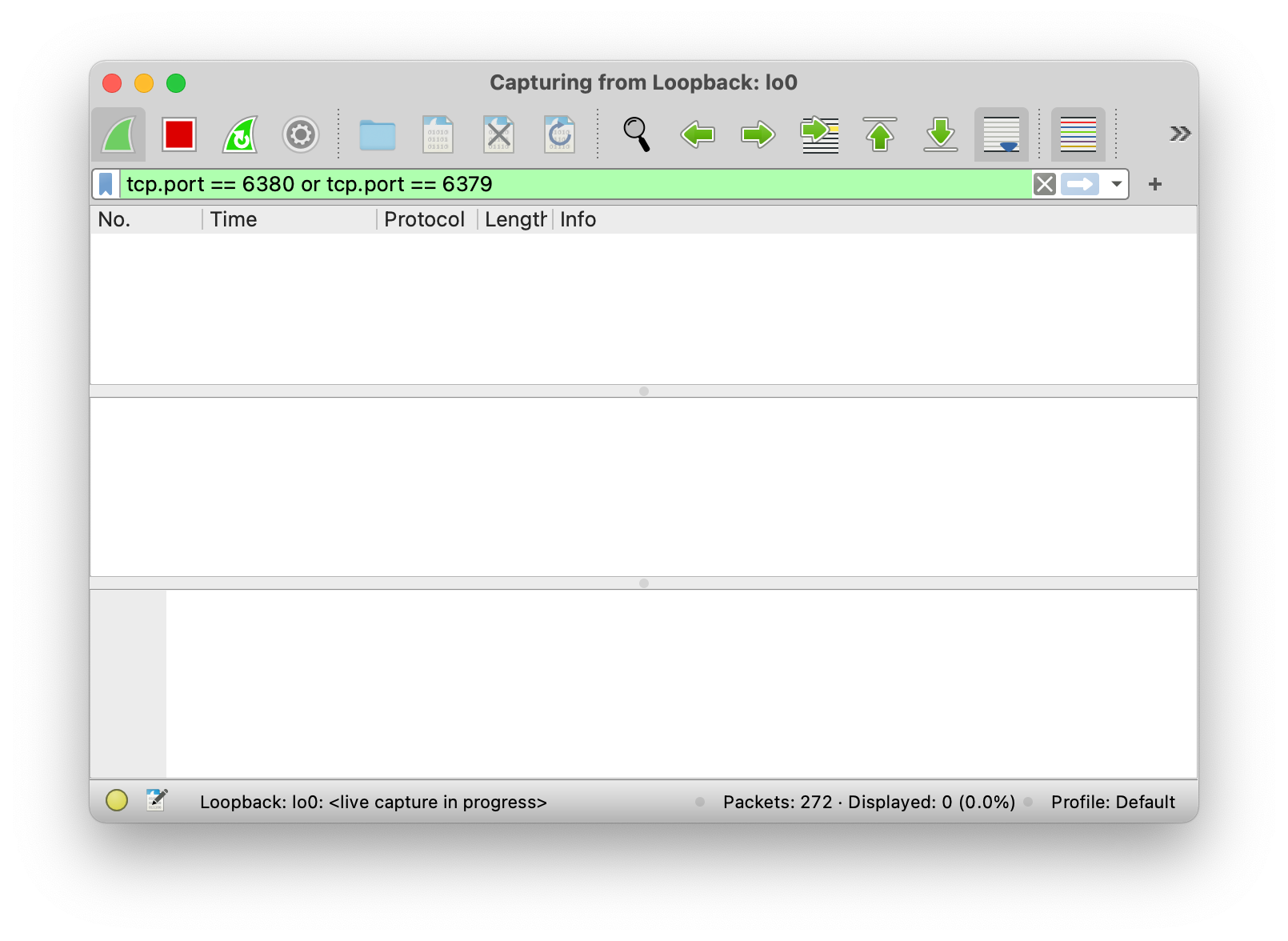
Loopback: lo0, and not something like Wi-Fi: en0.
Using tcpdump to capture and display TCP traffic
terminal
man tcpdump for more information.
2. Start your redis server implementation (on port 6379)
You’ll find instructions for this in your repository’s README (like here). Your server will run onport 6379, which is the port we’ve configured Wireshark to capture data on.
3. Start the official redis server implementation (on port 6380)
Runredis-server --port 6380 to do this.
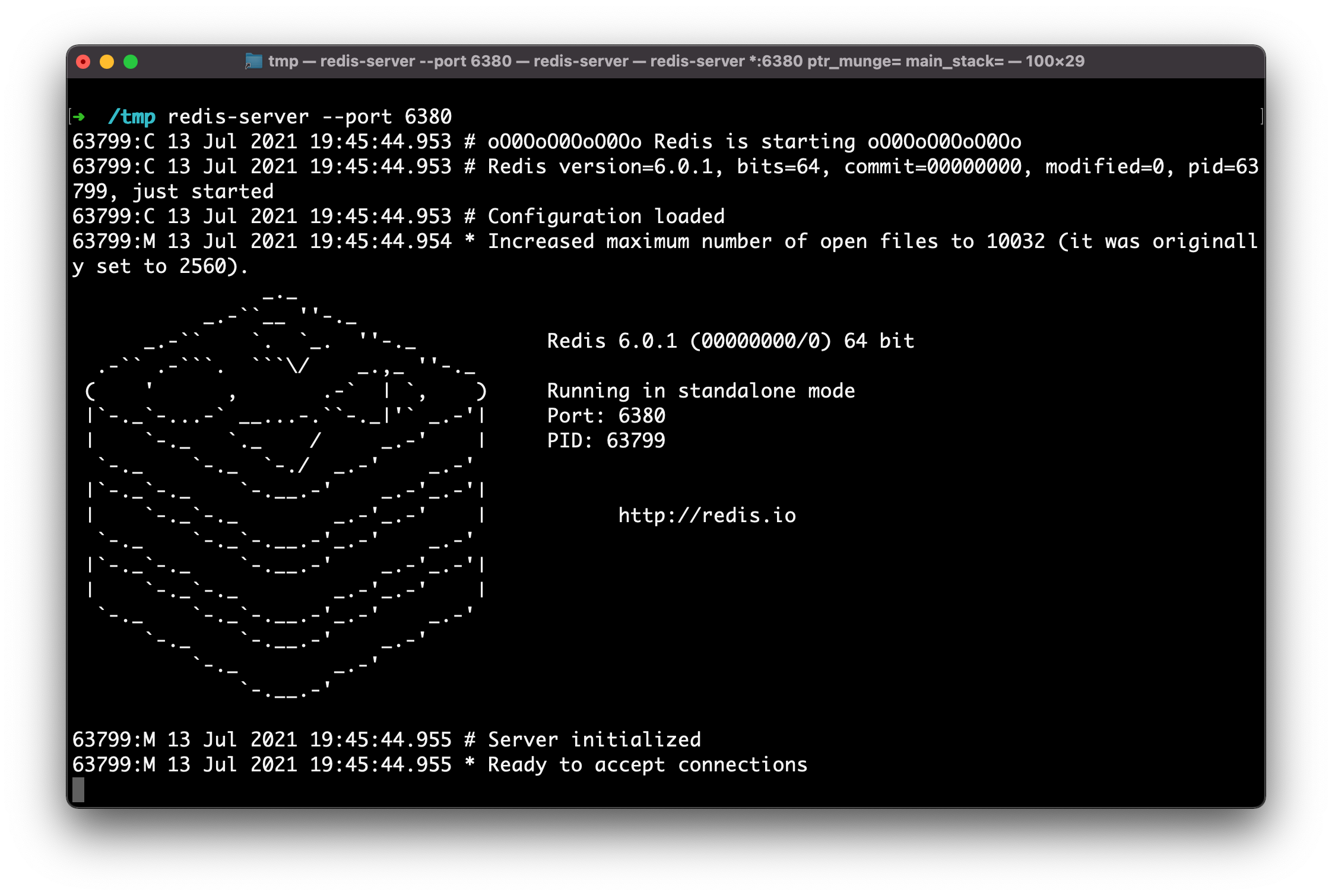
Terminal
Terminal
Note: You can also use the redis-cli interactive mode / REPL, but keep in mind that it sends a COMMAND command when it boots, which we don’t implement in the Redis challenge.
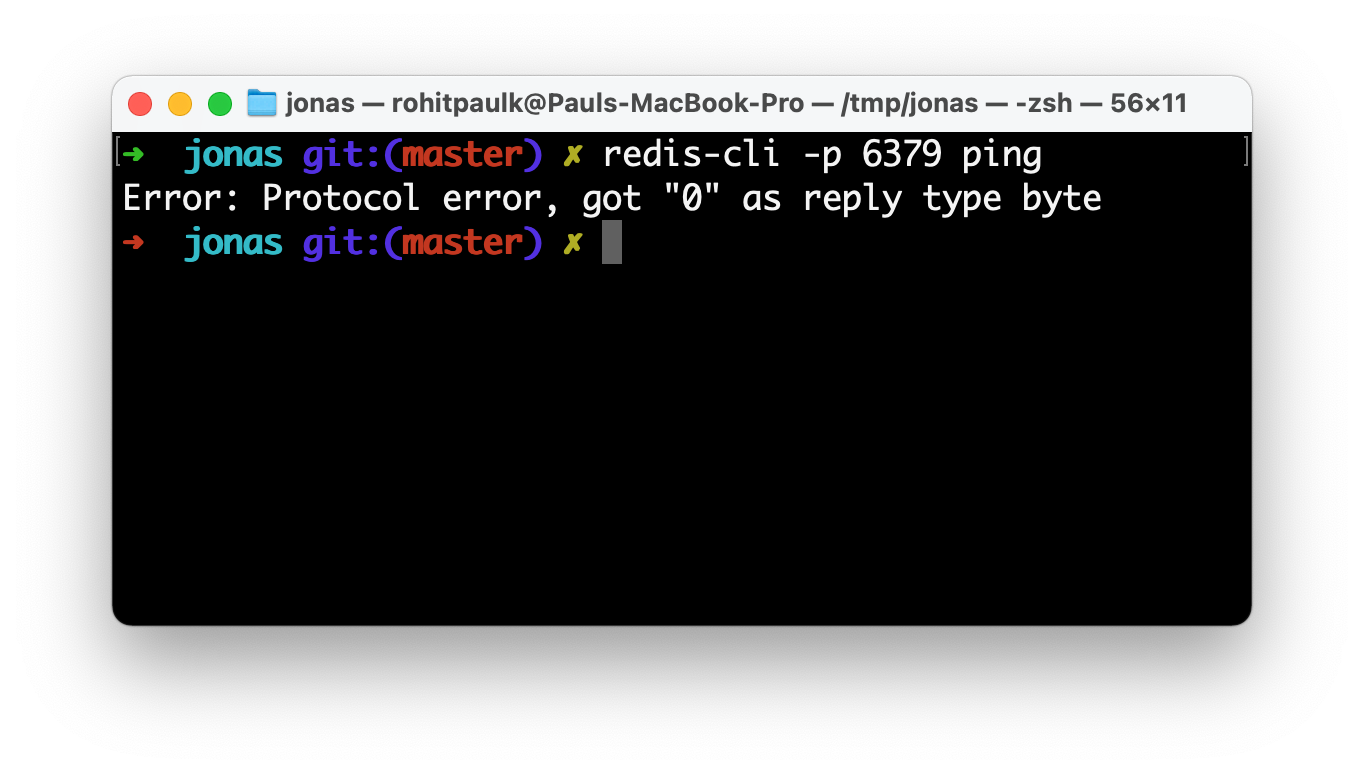
4. View capture data in Wireshark
Once you’ve sent a few commands, head back to Wireshark and you’ll now see some captured packets. You can inspect these to see exactly what data your implementation responded with.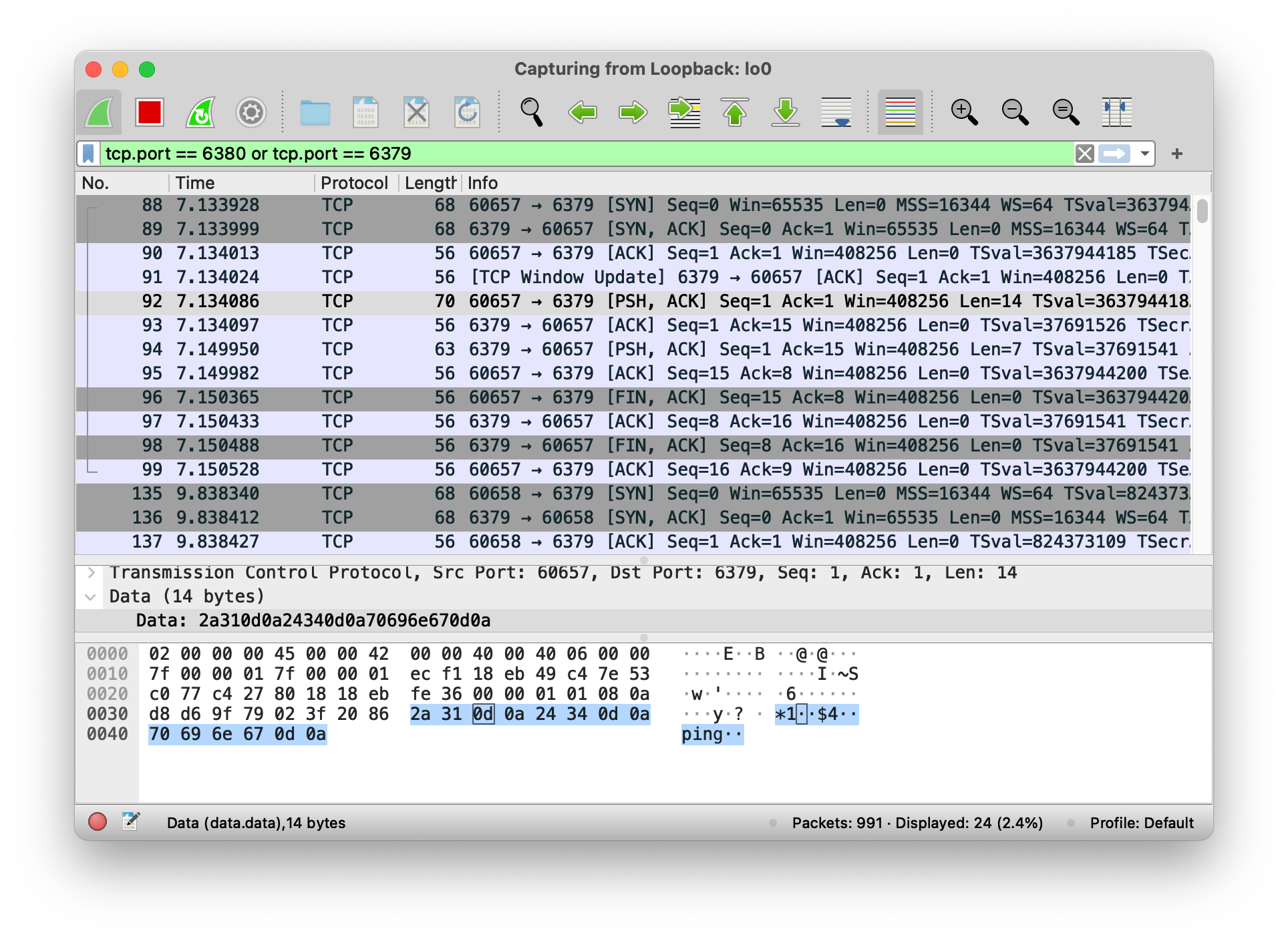
View capture data from tcpdump
tcpdump can output all the same information as Wireshark. For example, when sending the PING command, look for$4..PING.. and +PONG.. in the captured data.
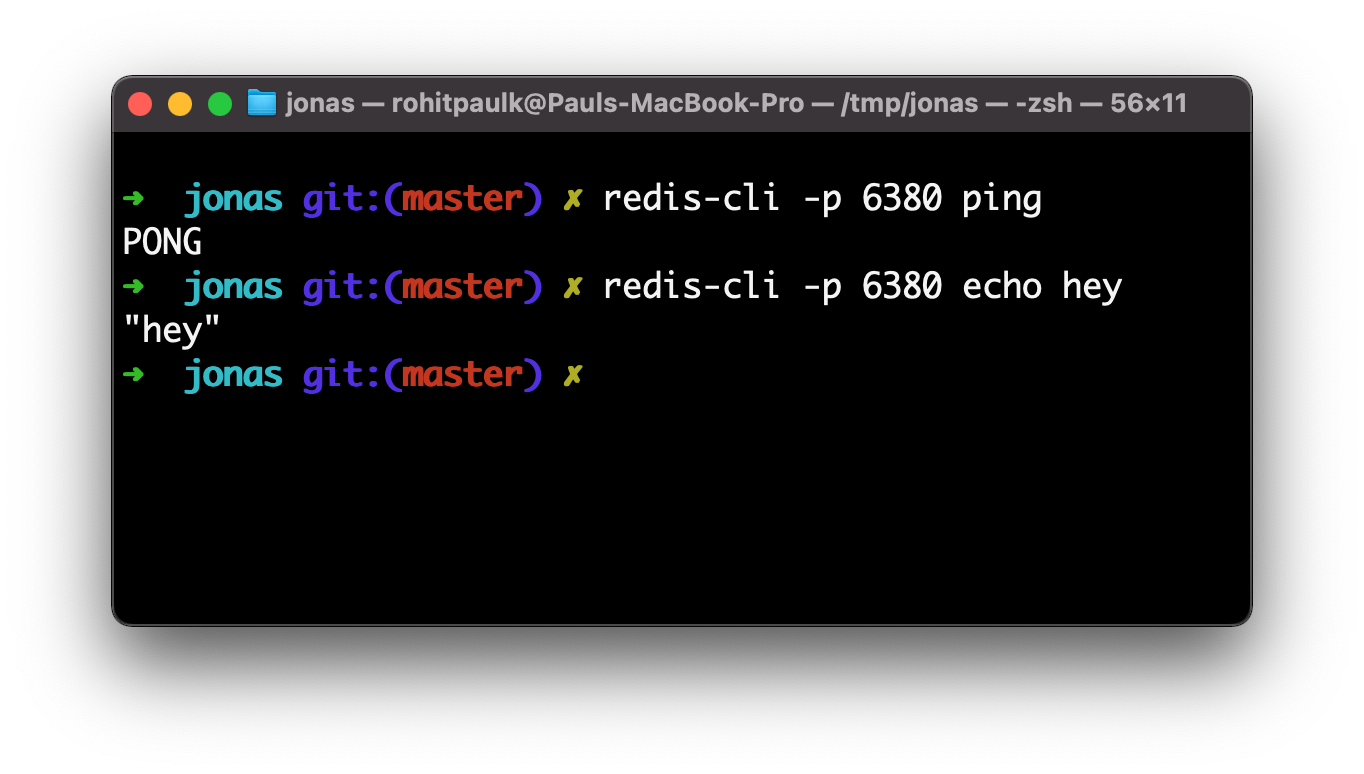
5. Compare with official redis implementation
Now that you know exactly what data your Redis server is sending, you can compare it with the official redis implementation to verify that it is working properly. Send commands usingredis-cli -p 6380 <command>.
If everything seems correct and you’re still seeing test failures, it’s possible that the Codecrafters tester program is at fault. Please let us know at hello@codecrafters.io if that’s the case!